Artificial intelligence is often hailed as a superpower, driving unprecedented innovation across nearly every industry — and for good reason. Yet, with this extraordinary progress comes a pressing question: is AI encroaching on our privacy?
AI has captivated the global imagination, promising to transform business, reshape society, and unlock new levels of efficiency. But behind the enthusiasm lies growing unease. Concerns around job displacement, consumer manipulation, and malicious applications have begun to surface. The speed of AI advancement has outpaced our collective understanding, highlighting the urgent need for clear governance and responsible implementation.
Lately, privacy concerns have dominated headlines, reinforcing one undeniable truth: safeguarding consumer data must be a top priority in every AI strategy. Curious how your AI strategy measures up when it comes to privacy? Let’s talk. Book a free consultation with our team — and partner with us to build compliant, future-proof AI solutions that inspire trust and drive innovation.

A pulse check on AI and privacy in 2025
The heady growth of generative AI tools has revived concerns about the security of AI technology. The data chills it triggers have been long plaguing AI adopters — except they’re now exacerbated by unique gen AI capabilities.
Inaccuracy, cybersecurity problems, intellectual property infringement, and lack of explainability are some of the most common generative AI privacy concerns that refrain 50% of organizations from scaling gen AI responsibly.
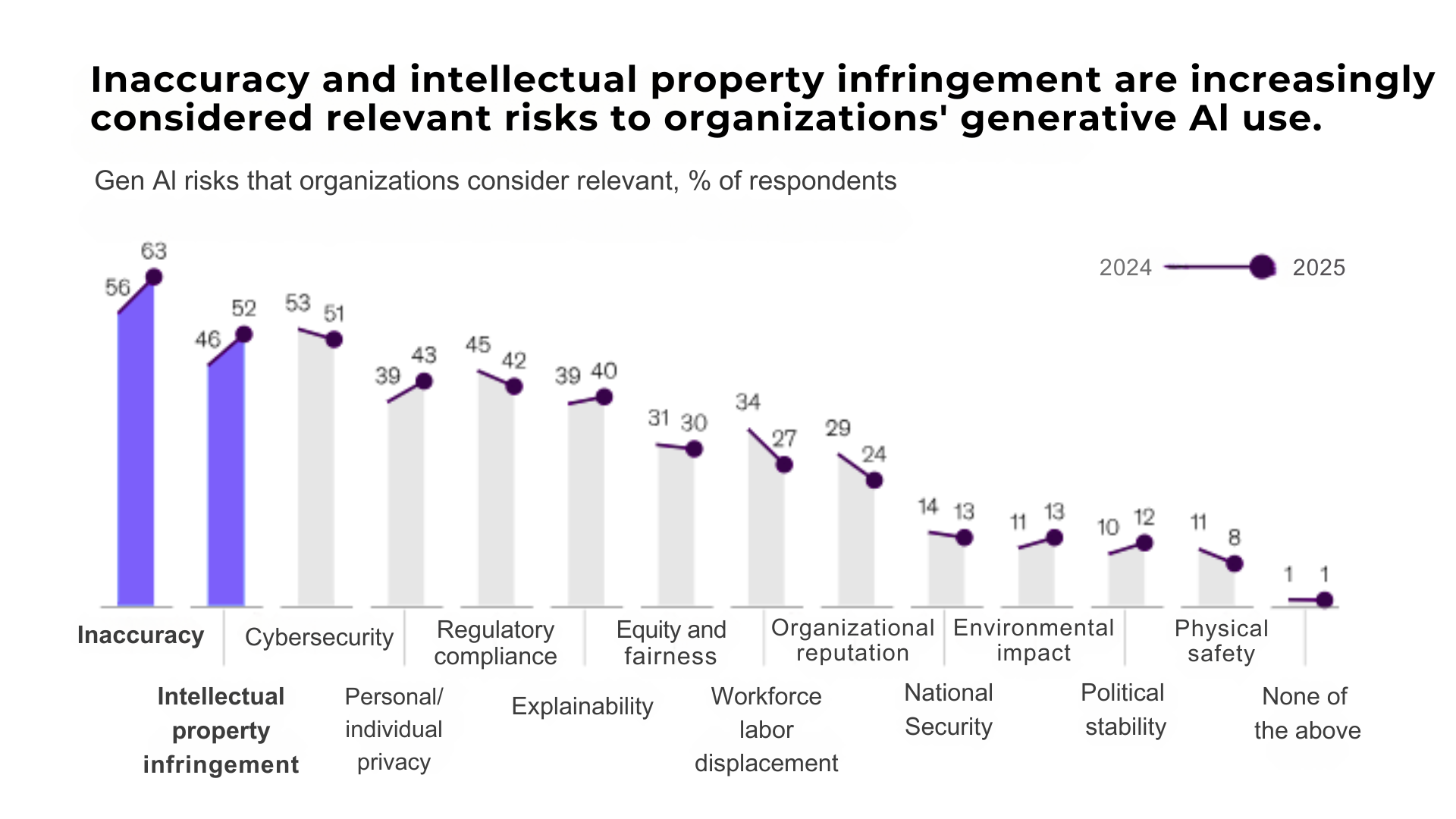
The worldwide community is echoing a security-focused approach of AI leading players, with a sweeping set of new regulations and acts advocating for more responsible AI development. These global efforts are initiated by actors ranging from the European Commission to the Organization for Economic Co-operation and Development to consortia like the Global Partnership on AI.
The dark side of AI: how can it jeopardize your organization’s data security?
No matter what type of AI solutions you are integrating into your business, prebuilt AI applications or self-built ones, the adoption of AI systems demands a heightened level of vigilance. When left unattended, AI-related privacy risks can metastasize, potentially causing a range of dire consequences, including regulatory fines, algorithmic bias, and other pitfalls.
Unclear control over data usage and access
Once your data flows into a generative AI system, it becomes challenging to track how it’s being handled and who can access it. Vague data ownership and undefined permissions — especially within third-party systems — make it difficult to enforce privacy. Add in the “black box” nature of many models, and you’re relying on external security practices that may not meet your company’s standards.
Your data, their training fuel
By signing up for a vendor-powered AI solution, organizations often unknowingly allow their data to be reused for training broader foundational models. Instead of being confined to your use case, your inputs can be absorbed into the vendor’s system — raising red flags around privacy and intellectual property. This practice can also backfire, introducing outside biases into your model’s behavior.
Re-identification of anonymized data
Even when personal data is scrubbed of identifiers, it doesn’t guarantee safety. Advanced AI systems can reconstruct user identities through behavioral patterns, effectively reversing anonymization. Worse yet, some models struggle with anonymizing data accurately, leading to potential breaches and compliance failures.
Weak links in the AI supply chain
AI ecosystems are made up of various layers — from the hardware and data sources to the model itself. Each component must be secured. Without holistic protection, one compromised element can corrupt the entire system — resulting in skewed outputs, biased decisions, or poisoned data sets.
While companies grapple with AI privacy challenges, real-world solutions show what’s possible. McFarland Johnson faced an overwhelming volume of documents across multiple divisions, slowing decision-making and risking inconsistencies in client deliverables. With Amazon Q, Dedicatted automated routine reports, centralized historical knowledge, and implemented role-based access controls, all while keeping sensitive data secure. Employees now save hours each week, workflows are more accurate, and AI-generated insights come with traceable links to source documents for full transparency. Explore the full AI transformation in our case study here

6 practices to wipe out AI data privacy concerns
While some companies grapple with AI risk management, 68% of high performers address gen-AI-related concerns head-on by locking risk management best practices into their AI strategies.
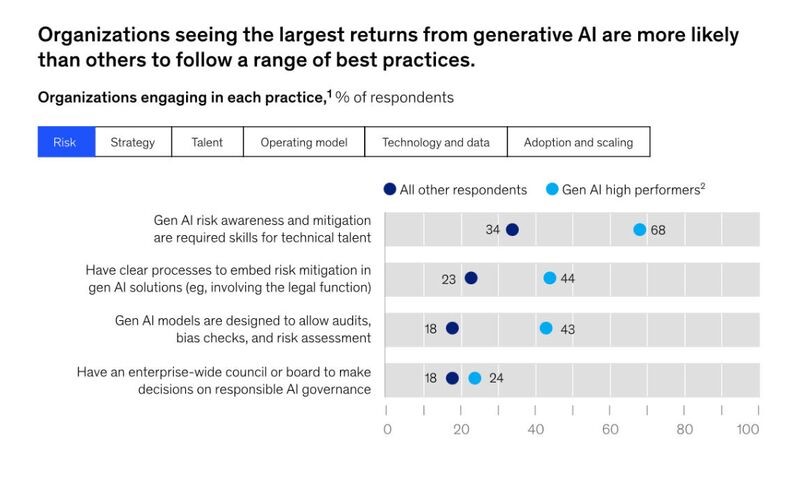
Standards and regulations provide a strong ground zero for data privacy in smart systems, but putting foundational principles in action also requires practical strategies. Below, our AI team has curated six battle-tested practices to effectively manage AI and privacy concerns.
1. Establish AI vulnerability management strategy
Just like any tech solution, an AI tool can have technology-specific vulnerabilities that spawn biases, trigger security branches, and reveal sensitive data to the prying eyes. To prevent this havoc, you need a cyclical, comprehensive vulnerability management process in place that focuses on the three core components of any AI system, including its inputs, model, and outputs.
- Input vulnerability management — by validating the input and implementing granular data access controls, you can minimize the risk of the input vulnerability.
- Model vulnerability management — threat modeling will help you harden your model by mitigating known documented threats. If you have commercial generative AI models in your infrastructure, make sure to perform close inspection of data sources, terms of use, and third-party libraries to prevent bias and vulnerabilities from permeating your systems.
- Output vulnerability management — strip the output of sensitive data or hidden code to make sure nobody can infer sensitive information and to mitigate cross-site vulnerabilities.
2. Take a hard stance on AI security governance
Along with vulnerability management, you need a secure foundation for your AI workloads, rooted in the wraparound security governance practices. Thus, your security policies, standards, and roles shouldn’t be confined to proprietary models but also extend to commercial and open-source models.
Water-tight security starts with a strong AI environment, amplified with encryption, multi-factor authentication, and alignment to best industry frameworks such as NIST AI RMF.
3. Build in a threat detection program
To defend your AI set-up against cyber attacks, you should apply a three-sided threat detection and mitigation strategy that addresses potential data threats, model weaknesses, and involuntary data leaks in the model’s outputs. Such practices as data sanitization, threat modeling, and automated security testing will help your AI team to pinpoint and neutralize potential security threats or unexpected behaviors in AI workloads.
4. Secure the infrastructure behind AI
Manual security practices might do the trick for small environments, but complex and ever-evolving AI workloads demand an MLOps approach. The latter provides a baseline and tools to automate security tasks, usher in best practices, and continuously improve the security posture of AI workloads.
Among other things, MLOps helps companies integrate a holistic API security management framework that solidifies authentication and authorization practices, input validation, and monitoring. You can also design MLOps workflows to encrypt data transfers between different parts of the AI system across networks and servers. Using CI/CD pipelines, you can securely transfer your data between development, testing, and production environments.

5. Keep your AI data safe and secure
Data that powers your machine learning models and algorithms is susceptible to a broader range of attacks and security breaches. That’s why end-to-end data protection is a critical priority that should be implemented throughout the entire AI development process — from initial data collection to model training and deployment.
Here are some of the data safeguarding techniques you can leverage for your AI projects:
- Data tokenization — protect sensitive data by replacing it with non-sensitive data tokens as surrogates for the actual information.
- Holistic data security — make sure you secure all data used for AI development, including at-rest, in-transit and in-use data.
- Loss prevention — apply data loss prevention (DLP) techniques to prevent sensitive or confidential data from being lost, stolen, or leaked outside the perimeter.
- Security level assessment — continuously monitor the sensitivity of your model’s outputs and take corrective actions if the sensitivity level increases. Extra vigilance won’t hurt when using new input datasets for training or inference.
6. Emphasize security during AI software development lifecycle
Last but not least, your ML consulting and development team should create a safe, controllable engineering environment, complete with secure model storage, data auditability, and limited access to model and data backups.
Security scans should be integrated into data and model pipelines throughout the entire process, from data pre-processing to model deployment. Model developers should also run prompt testing locally in their environment and also in the CI/CD pipelines to assess how the model responds to different user inputs and nip potential biases or unintended behavior in the bud.
Balancing innovation and privacy
To remain top of the game amidst the growing competition, companies in nearly every industry are venturing into AI development to tap its innovative potential. But with great power comes great responsibility. As they pioneer AI-driven innovation, organizations must also address the evolving risks associated with AI’s rapid development.
In Dedicatted , we understand the importance of balancing innovation, data privacy, and ethical considerations in AI development lies in ensuring sustainable technological progress while safeguarding individual rights and societal norms. Compliance fosters transparency and accountability in AI operations, leading to more reliable technology.
Contact us to create more responsible and user-centric AI solutions that are viable in a global market.


